Cloud computing has become the backbone of modern businesses, enabling organizations to store, process, and share data more efficiently than ever before. From small startups to global corporations, cloud platforms offer scalability, flexibility, and cost-effectiveness that traditional IT systems cannot match. However, as more data moves to the cloud, cybersecurity threats have also evolved, becoming more sophisticated and potentially more damaging.
Data Breaches and Unauthorized Access
One of the most pressing cybersecurity threats in the cloud is the risk of data breaches. Hackers target cloud storage systems to gain access to sensitive information, including customer details, financial records, and intellectual property. Weak access controls or poorly managed credentials can make systems vulnerable.
Risks include:
- Theft of personal or financial data
- Exposure of confidential business information
- Reputational damage and loss of customer trust
Insider Threats
Not all cybersecurity risks come from outside the organization. Insider threats, whether intentional or accidental, can be just as harmful. Employees with access to sensitive cloud data can misuse it or fall victim to phishing attacks, unknowingly granting access to malicious actors.
Key issues with insider threats:
- Malicious employees stealing data for personal gain
- Accidental sharing of sensitive files
- Lack of monitoring for user activity in the cloud
Insecure APIs and Application Vulnerabilities
Cloud services rely on application programming interfaces (APIs) to connect applications and enable data exchange. If these APIs are not properly secured, cybercriminals can exploit them to access data or disrupt services.
Common problems include:
- Poorly designed or unencrypted APIs
- Lack of authentication and authorization controls
- Vulnerabilities in third-party integrations
Misconfiguration of Cloud Services
Cloud platforms often provide a wide range of settings for security and privacy. If these configurations are not properly set, data may be exposed publicly without the organization realizing it. Misconfiguration errors are one of the leading causes of cloud-related breaches.
Examples of misconfiguration risks:
- Publicly accessible storage buckets
- Weak encryption settings
- Overly permissive access controls
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
Cloud services can be targeted by DoS and DDoS attacks, where hackers overwhelm servers with excessive traffic, making them slow or completely unavailable. This can disrupt operations, cause financial losses, and affect customer experience.
Impact of DoS/DDoS on cloud environments:
- Service downtime and customer frustration
- Increased costs for additional bandwidth
- Potential loss of revenue during outages
Data Loss and Recovery Challenges
While cloud providers implement backup systems, accidental deletion, hardware failures, or malicious attacks can still lead to data loss. In some cases, recovering lost data may be difficult, especially if no proper backup plan is in place.
Factors contributing to data loss:
- Incomplete backup policies
- Ransomware encrypting files
- Lack of data retention strategies
Shared Responsibility Model Confusion
Cloud security operates under a shared responsibility model, where the provider secures the infrastructure, and the customer secures their data and applications. Misunderstanding this model can leave gaps in protection.
Key points in the shared responsibility model:
- Providers secure the physical infrastructure and network
- Customers must secure access controls, encryption, and user data
- Security gaps occur when responsibilities are unclear
Protecting Against Cloud Cybersecurity Threats
Organizations can reduce risks by adopting strong security practices for their cloud systems. This includes:
- Implementing multi-factor authentication for all accounts
- Encrypting data both in transit and at rest
- Regularly auditing and updating cloud configurations
- Using security monitoring tools to detect suspicious activity
- Providing employee training on phishing and data handling
Final Thoughts
The cloud offers incredible benefits, but it also introduces unique cybersecurity challenges that must be addressed proactively. As threats become more advanced, businesses need to combine technology, policies, and user awareness to secure their cloud environments.
By understanding the risks and implementing robust security measures, organizations can fully embrace cloud computing without compromising data safety or customer trust.

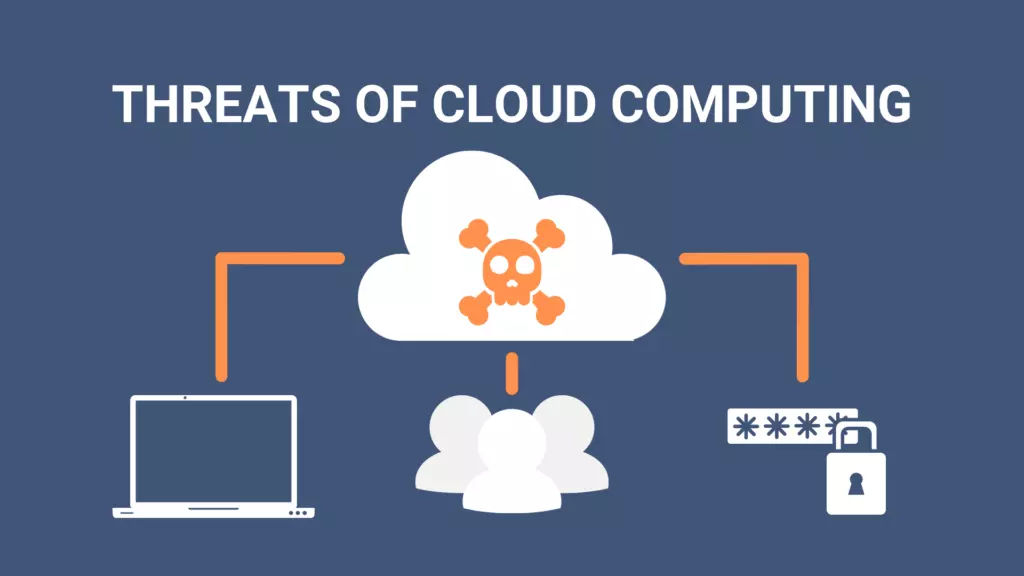
As much as cloud computing is promising, certain measures already discussed in the article would go a long way to ensure security